In 2026, cyber threats aren’t just evolving—they are outpacing traditional defences. The sophistication and frequency of cyber threats are continuing to rise, targeting vulnerabilities across cloud environments, remote work infrastructures, and more. From AI-generated phishing campaigns to deepfake-driven social engineering, attackers are leveraging emerging technologies faster than many organisations can respond. Organisations who will fail to adapt will be at greater risk of data breaches, financial loss, and reputational damage.
Unlike old days, the threat landscape has become more intelligent, more automated, and far more unpredictable, making it critical for businesses to rethink how they approach cybersecurity—before any disaster happens.
At Exigo Tech, we understand that staying ahead of cyber threats requires more than reactive solutions—it demands strategic vision, innovation, and a customised approach. Hence, we work at the intersection of innovation and security, helping organisations anticipate risks and respond with confidence. In this blog, we will explore the top 9 cybersecurity threats that are defining 2026, and more importantly, outline the strategies, tools, and partnerships needed to neutralise them. It’s not about fear—it’s about preparation, clarity, and building cyber resilience from the inside out.
Top 9 Cybersecurity Threats in 206
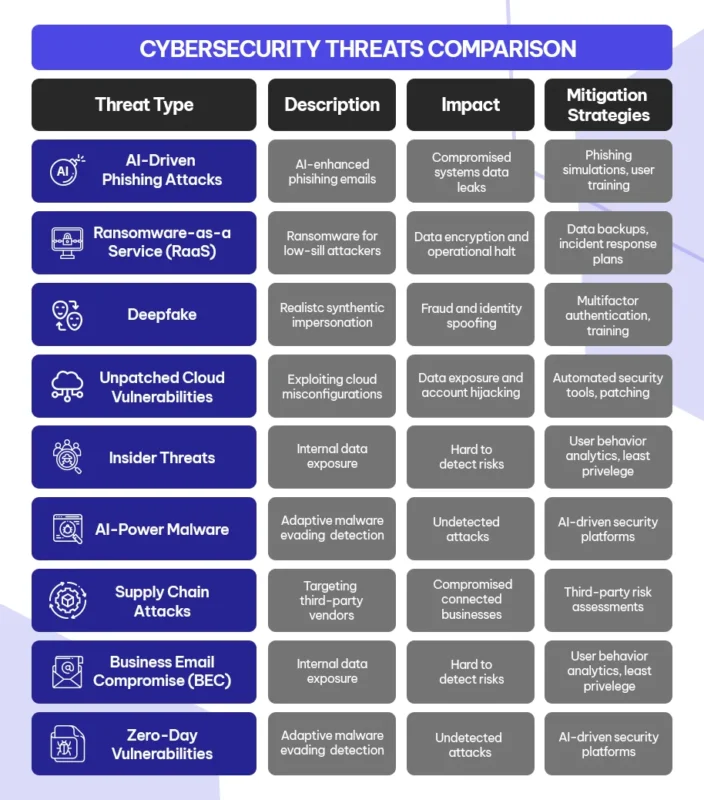
1. AI-Driven Phishing Attacks
What it is:
Phishing has always been a go-to tactic for cybercriminals, but in 2026, it’s been enhanced by artificial intelligence. Attackers now use AI to craft hyper-personalised, grammatically perfect, and context-aware phishing emails and messages. These campaigns are nearly impossible to separate from legitimate communication and are often launched at scale across multiple channels—email, chat apps, and even voice.
Why it matters:
With remote and hybrid work still dominant, the human attack surface is larger than ever. A single employee falling for an AI-generated phishing email can compromise entire systems, leak sensitive data, or open the door for ransomware.
How to mitigate:
Regular phishing simulations, real-time threat detection tools, and ongoing user training are essential. Implementing advanced email filtering, zero-trust policies, and anomaly detection can reduce the risk significantly.
2. Ransomware-as-a-Service (RaaS)
What it is:
Ransomware isn’t just in the hands of elite hackers anymore. In 2026, it’s a business model—Ransomware-as-a-Service. With pre-built malware kits available on the dark web, even low-skill attackers can launch sophisticated ransomware attacks for a small fee or revenue share.
Why it matters:
The barrier to entry has dropped, but the damage hasn’t. Encrypted data, halted operations, and costly ransom demands can damage an organisation overnight—especially those without proper incident response plans.
How to mitigate:
Regular data backups, strict access controls, endpoint protection, and rapid incident response protocols are key. Don’t pay the ransom—prepare for it.
3. Deepfake
What it is:
Deepfake technology has reached alarming levels of realism. Attackers are now using synthetic voices and videos to impersonate executives, fool authentication systems, and manipulate digital identities.
Why it matters:
Traditional identity verification methods—like voice, video, or static biometrics—are becoming easier to spoof. This makes executive impersonation, fraud, and social engineering attacks more convincing than ever.
How to mitigate:
Implement multifactor authentication (MFA), continuous biometric authentication, and employee training to verify requests through trusted channels.
4. Exploitation of Unpatched Cloud Vulnerabilities
What it is:
Cloud adoption is nearly universal, but security gaps persist—often due to misconfigurations or delayed patching. Attackers scan for these weak spots and exploit them at scale.
Why it matters:
Cloud environments host critical data and applications. A single misconfiguration or missed update can lead to massive data exposure or account hijacking.
How to mitigate:
Use automated tools for cloud security posture management, apply patches promptly, and monitor access rights regularly.
5. Insider Threats (Malicious and Accidental)
What it is:
Not all threats come from outside. Employees, contractors, or partners—intentionally or unintentionally—can expose sensitive data, misconfigure systems, or fall for scams.
Why it matters:
Insider threats are often very hard to detect and can bypass most external defences, making them one of the most dangerous types of cyber risk.
How to mitigate:
Deploy user behaviour analytics, apply the principle of least privilege, and build a security-aware culture across the organisation.
6. AI-Powered Malware
What it is:
Just like defenders use AI to catch threats, attackers use it to create adaptive, advanced malware that learns from its environment and changes behaviour to avoid detection.
Why it matters:
Traditional antivirus and signature-based systems can’t keep up. AI-powered malware can bypass these tools and remain undetected for longer periods.
How to mitigate:
Adopt AI-driven security platforms, implement behaviour-based detection, and continuously update threat models.
7. Supply Chain Attacks
What it is:
Attackers target third-party vendors or software providers to compromise your environment indirectly. These attacks are stealthy, hard to detect, and can bypass traditional security perimeters.
Why it matters:
A single compromised supplier can expose hundreds of connected businesses. In 2026, digital supply chains are more interconnected than ever—making them a high-value target.
How to mitigate:
Conduct third-party risk assessments, monitor for anomalous activity, and enforce zero-trust access policies for vendors.
8. Business Email Compromise (BEC)
What it is:
BEC is a targeted form of cyberattack where attackers impersonate executives, vendors, or trusted partners via email to trick employees into transferring money, sharing credentials, or revealing sensitive information. In 2026, these attacks are more convincing than ever—often powered by AI and real-time social engineering.
Why it matters:
Unlike broad phishing attempts, BEC attacks are highly targeted and can result in significant financial losses. They are also harder to detect because they often use legitimate-looking domains or even compromised internal accounts.
How to mitigate:
Enable multi-factor authentication (MFA), educate employees on red flags, and implement internal approval workflows for financial transactions or sensitive data sharing.
9. Zero-Day Vulnerabilities
What it is:
Zero-days are previously unknown vulnerabilities with no available patches. Attackers exploit them before vendors or users even know the flaw exists.
Why it matters:
These attacks are highly dangerous and often used in targeted campaigns. By the time a patch is released, the damage may already be done.
How to mitigate:
Layered defences, endpoint detection and response (EDR), and threat intelligence can help reduce exposure and response time.


Stay Ahead of Cyber Threats
Explore our award-winning cybersecurity solutions to protect your organisation from evolving cyberattacks.
Get StartedHow to Strengthen Your Cybersecurity Posture with Exigo Tech
Defending against today’s threats takes more than just firewalls and antivirus software—it requires a proactive, intelligence-driven, and adaptive strategy. At Exigo Tech, we don’t just react to cyber threats—we anticipate them. That’s why we have been recognised as a finalist at the Australian Cyber Awards 2025 in two major categories: Cloud Service Provider of the Year and CISO of the Year. This recognition reflects our leadership, innovation, and real-world impact in helping businesses build cyber resilience.
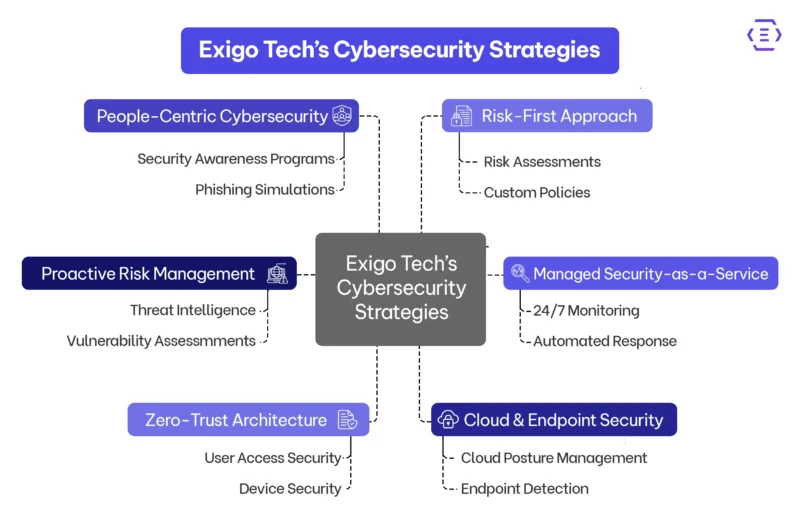
Here’s how Exigo Tech helps you build that resilience:
1. Proactive Risk Management
We help businesses shift from reactive firefighting to proactive risk identification. Through advanced threat intelligence, vulnerability assessments, and predictive analytics, we identify potential weaknesses before attackers do—minimising risk and enhancing decision-making.
2. Managed Security-as-a-Service (MSaaS)
Cybersecurity needs to be always-on, not 9-to-5. With our MSaaS offering, you get 24/7 monitoring, automated threat response, and expert-led incident management—all delivered through a cost-effective, scalable framework. It’s ideal for businesses that want enterprise-grade protection without much cost and building an in-house security team.
3. Zero-Trust Architecture
Trust nothing, verify everything. We design and implement Zero Trust frameworks that secure access at every level—users, devices, applications, and networks—ensuring that even if attackers breach one layer, they hit a wall at the next.
4. Cloud & Endpoint Security
Whether you operate in a hybrid, multi-cloud, or remote-first environment, we ensure your infrastructure is monitored, updated, and protected around the clock. From cloud posture management to endpoint detection and response (EDR), we have got every corner covered.
5. People-Centric Cybersecurity
Technology is only as strong as the people using it. That’s why we integrate security awareness programs, phishing simulations, and insider threat mitigation strategies—so your team becomes your strongest defence, not a weak link.
6. Risk-First, Not Tool-First
Cybersecurity isn’t about adding more tools—it’s about aligning security with your business priorities. We begin with risk assessments, build policies around what matters most, and customise protection accordingly—so every investment makes sense.
Feel free to reach out to us at or call us at 1300 EXIGOTECH (394 468) to get more information.


Let’s Build a Stronger Cybersecurity Posture
Get our MSaaS offering with zero upfront cost and ensure your business remains resilient against sophisticated cyberattacks.
Explore More Here
 Australia
Australia Singapore
Singapore Philippines
Philippines India
India Niten Devalia | Apr 14, 2025
Niten Devalia | Apr 14, 2025



 Exigo Tech - Ask AI
Exigo Tech - Ask AI







