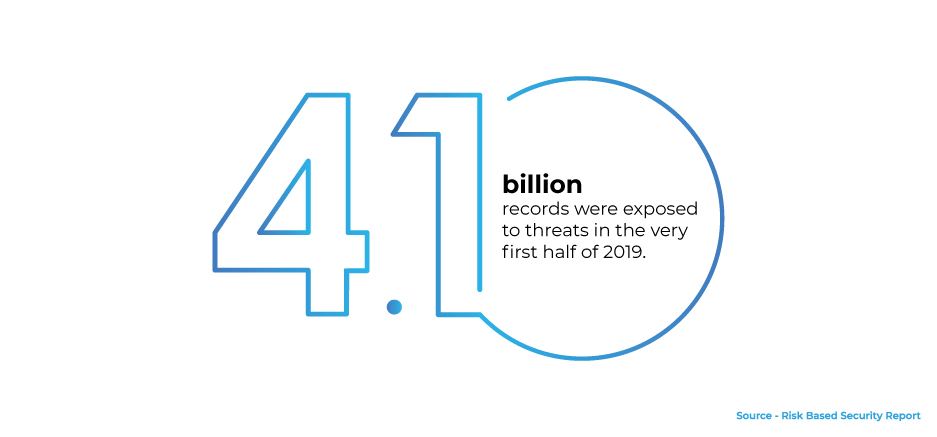
Cloud computing has always remained one of the top priorities of businesses in Australia. No doubt, the professionals are always eyeing out the solutions which are available at reduced costs. But cloud offers a range of flexibilities such as scalability, mobility and business agility which makes it a lucrative option for decision-makers. Also, the constant increase in the use of artificial intelligence and the internet of things (IoT) has spiked the importance and usage of cloud computing. Although there is an upsurge in the demand for cloud computing services, businesses still doubt the security aspect of it. The corporate world is skeptic regarding the security of the data stored because of cyber attacks and breaches becoming rampant.
Steps taken by Microsoft to prevent data theft in Azure
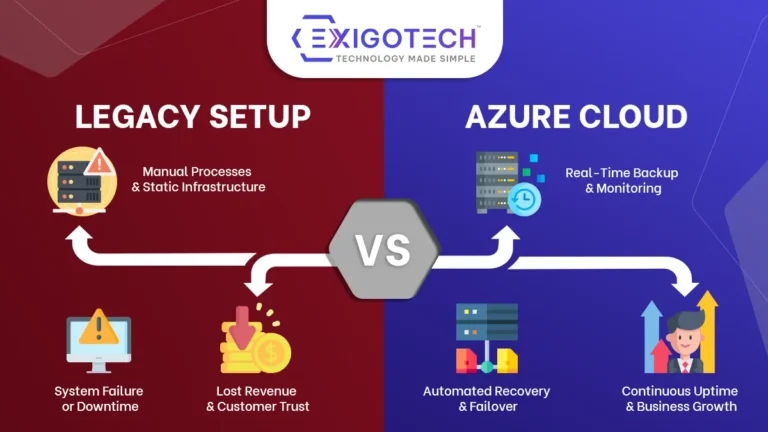
Azure, a product from the Microsoft suite, offers numerous services such as analytics, computing, database, mobile networking, storage and web. All of these services work together to make it feasible for organisations to build and manage IoT applications as well as mobile or web applications. Azure offers a bundle of features and automated processes which reduces human errors which mostly are the sole reason for security breaches. Microsoft has designed its datacenters with tight physical security measures to ensure that these are resilient to survive complicated cyberattacks. Multifactor authentication, an incident response team, constant monitoring and logging data are some of the other measures taken by Microsoft to ensure the security of your data stored in the cloud. Let’s dig deep into these and understand more about them:
-
Physical security:
Microsoft has multilayered protection to ensure that any unauthorised personnel is not given physical access of the datacenters where your customer’s data is stored. Microsoft offers security at different places such as at the facility perimeter and building perimeter, in the particular building and also for different floors in the datacenter.
-
Security design and operations:
Microsoft ensures that at every step of Azure cloud creation, the security of the confidential data is taken care of. The code development adheres to the Microsoft Security Development Lifecycle (SDL) which is followed by the technology giant during the planning, design, development and the deploying phases. Azure also takes measures to assure that data security is monitored during operations and the support phase too. Another critical measure taken by Microsoft to harden its cloud infrastructure is to assume the breach. In this method, they assume that hackers are able to break into their secured cloud and then they think about the counter strategy to mitigate the effects of the breach.
-
An incident response team:
This measure is based pretty much on the assume breach step. However, this team comes into play once the breach has successfully taken place. They follow a step by step approach which starts by detecting the breach, assessing the impact of the breach, diagnosing if the customer data has already been exposed to the hacker and tailoring a mitigation plan before closing the issue. To give you a complete overview of the attack, the team gives insights on the source of the attack and the information that is impacted due to the attack. They also suggest certain steps that you can take to avoid future attacks. Azure security center offers a complete view of the security structure of the hybrid computing resources as well.
-
Management and control of the user access rights:
Microsoft allows the Azure cloud users to restrict access to network environments, data and applications according to personnel’s assignment, authorisation and requirement. The cloud network is sealed for all the possible security breaches with a multi-factor authentication method. Also, you have the flexibility to decide if any employee would be able to access the cloud environment from any personal device.
-
Data protection:
Considering the fact that your confidential data is your digital asset, Azure cloud allows you to safeguard your data stored in applications, platforms or systems with four specific methods. These methods are segregation, encryption, redundancy and destruction. As the word segregation suggests, in this method Azure ensures that your data is not combined with anyone else’s. Also, you have the flexibility to use various encryption models to assure that the confidentiality of your data is maintained. If you happen to delete any data from your Azure cloud, Microsoft follows an industry-standard process to erase all that data before initiating its reuse.
It is certain that after gaining some knowledge about the ways in which Microsoft Azure guarantees the security of your data, you still might be concerned regarding its confidentiality. We, a Microsoft Solutions Partner, will address all your concerns over a call or a face to face appointment. To get in touch with us today, you can send us an email at or call 1300 EXIGOTECH (394 468). Let’s work together to keep your cloud security concerns at bay!
 Australia
Australia Singapore
Singapore Philippines
Philippines India
India Vivek Trivedi | Nov 07, 2019
Vivek Trivedi | Nov 07, 2019