According to a report, 70% of security breaches start from an endpoint whether it is a PC, tablet, smartphone or POS terminals. And the COVID-19 situation has dramatically imposed a new normal where professionals are supposed to operate from anywhere, increasing the number of endpoints in any company’s IT stack. Furthermore, the technologies are intertwined with each other making it difficult for the IT teams to identify a breach. Furthermore, the bad actors are improving their methods to enter your organisation, adding to the difficulties of IT professionals.
The current situation pushes an organisation to change its thought process. Previously, the IT executive used to get a notification once the security of an endpoint is already being compromised. But now, businesses have to keep up with the pace at which the hackers are evolving otherwise they will increase the chances of their confidential data being leaked. Engaging your in-house team for taking care of the endpoints is not an ideal way out. Here is when, Exigo Tech – a leading managed security solutions provider can help you.
To start with, Exigo Tech houses a team of security engineers who are trained and skilled to offer numerous services, basically, they build an infrastructure to strengthen your organisation’s security stance. The services we deliver, include – 
-
Managed Detection and Response Services
We offer a mix of tools that are equipped with AI technologies to identify undetected threats and send notifications, so that you are able to take actions against them. Our teams also analyse these threats to accelerate the remediation actions across the network components and the endpoints stored in multi-cloud environments.
-
Host Intrusion Prevention
We scan your businesses’ technology environment on a regular basis to investigate new endpoints and see if there any patches that should be updated. We make it a point to upgrade the patches in a manner that your regular operations do not get interrupted. We send reports to the stakeholders to keep them informed about the health of their business endpoints.
-
Network Access Control Add-ons
We help you create policies that restrict access of any bad actors. We formulate these based on different parameters such as employee’s designation, location and device. With these policies in place, you can build a BYOD environment without any major security concerns. We as your managed security solution provider offer a host of solutions that allow you to block or remove any infected endpoint from your network on a temporary basis. You can give the varying level of access to your employees as per your requirements.
-
Application Block
We help you choose applications that can be a threat to your organisation’s security posture so that these can be blocked in your environment. The application control tools also enable you to block the access of those applications which you think are not ideal to be used in an office environment.
Strengthen Your Security Posture with a Managed Security Solutions Provider
I wouldn’t be exaggerating when I say that the endpoint security playground is getting dense. And the responsibilities of managed security solutions providers are going to increase by leaps and bounds. With the new financial year just around the corner, there would be some areas that would require our (solution provider’s) focus. These would include aligning the policies with the industry compliances and regulations, deploying endpoint encryption technologies and much more. Our teams keep upskilling themselves with the industry trends so that they can offer the best services to our clients. We strive to evolve at a pace that allows us to keep ourselves ahead of the hackers and we are able to secure your corporate endpoints. To safeguard your endpoints from any evolving cyber-attacks, call 1300 EXIGOTECH (394 468) or email at .
 Australia
Australia Singapore
Singapore Philippines
Philippines India
India Vivek Trivedi | Apr 23, 2021
Vivek Trivedi | Apr 23, 2021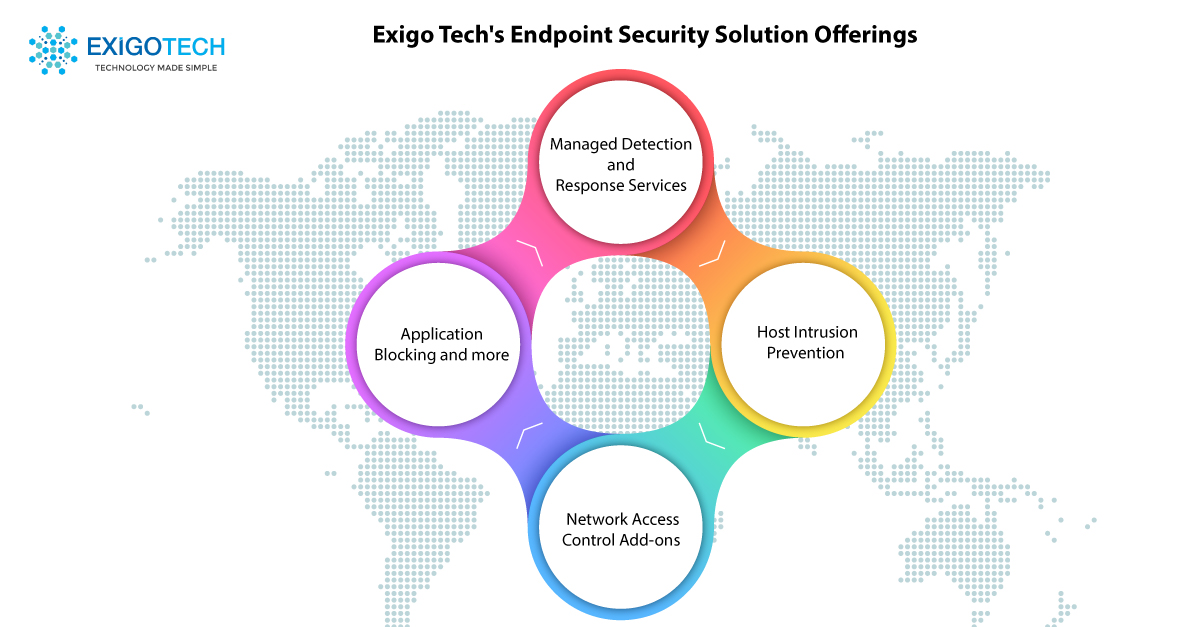



 Exigo Tech - Ask AI
Exigo Tech - Ask AI







