In my last article, I talked about IoT at length and also focused on its applications in the healthcare sector. Following on, in this post I want to concentrate on the effects of rapid adoption of the internet of things on healthcare professionals. It is certain that hospitals and other healthcare facilities are benefitting immensely from the proliferation of IoT in the industry. This fact also echoed in the report released by Gartner which stated that around 1 billion devices will be connected with each other by 2020. However, a report by Galus Australia states that the security market of IoT will see rapid growth of 34.10% CAGR during the period of 2019-26. The reports clearly imply that as much as the adoption of IoT has increased, the security concerns have also shot up.
Words of Wisdom for Healthcare Professionals
Many healthcare professionals think that if the features available in their connected devices are not secure then why are they there in the very first place. I do understand that the medical workforce is not technically sound but looking at the impact of the security breaches, it has become kind of crucial to train them for sealing the security loopholes. In such situations, educating them about all the potential risks associated with using a flawed or unsecured device/system is an apt solution. You cannot follow a one size fits all approach while tailoring a training program for your medical staff. For example, you need to explain the risks of keeping sensitive data in a smartphone to the hospital receptionist.
You need to tell your doctors the security concerns of connecting the heart monitoring machine with his smartphone for providing assistance from remote locations. Training professionals according to their work and experience will pique their interest and they will absorb the security principles. Also, by customising the training plan, you can leverage your staff’s experience and benefit from their technical knowledge. Setting up a training plan is not a walk in the park because your staff already have a lot on their plate and having training on the security of the internet of things may not top their priority list. But if given in bits and pieces and also on the relevant topics, you can actually succeed in conducting a training session.
Even if you have given enough training on the measures to be taken to ensure data security because of the connected devices, the ball remains in your court too. Once any of your devices are accessible on the internet, ensure that you find all the potential hazards and the malware that can actually enter your IoT ecosystem and steal the confidential data. Also, ensure that any device which is a part of your internet of things net is equipped with the latest security features. Never miss an update on these devices because updates may contain a patch for a security violation. When you have ensured that your workforce is quite aware about the security norms and you have secured the connected devices, the next step is to hold your cloud service provider accountable for providing a secured infrastructure. Make sure that the points through which your data is transmitted are secured enough and are regularly monitored by the cloud provider.
An Apt Solution for Both
Taking apt security measures is important and the responsibility of healthcare organisation as well as the device manufacture.
- Device Manufacturers:
There are several points to be considered when medical devices are designed for the internet of things framework.- Authenticate:
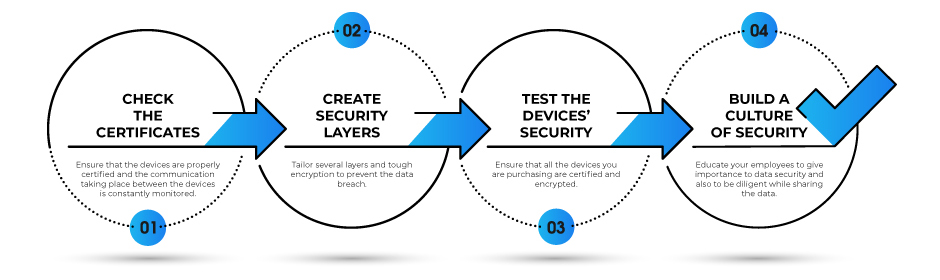
The medical devices should be authenticated with a certificate and should be proven suitable to work without any security leak in hospitals or healthcare institutes. The devices should be programmed in such a manner that only the one with proven identities can use them.
- Encrypt:
The manufacturers have to ensure that their devices are certified and can send encrypted data privately.
- Authenticate:
- Healthcare Institutes:
The medical institutions also need to follow several steps such as
Conclusion
Fortunately, there have been no solid cases where hackers could break into the IoT infrastructure and steal any confidential data. But this can happen in the very near future and therefore it is advisable to remain prepared if the storm strikes. Hospitals also have the legacy equipment and devices which are a potential loophole for hackers to enter. Therefore, diligence is the key when it comes to tailoring the cybersecurity strategy for any healthcare facility because a breach means that human life is at risk.
 Australia
Australia Singapore
Singapore Philippines
Philippines India
India Vivek Trivedi | Dec 12, 2019
Vivek Trivedi | Dec 12, 2019



 Exigo Tech - Ask AI
Exigo Tech - Ask AI







