Email phishing attacks are becoming quite a rampant method amongst hackers to breach your network. And there is no doubt in the fact that we all use emails for our professional and sometimes personal communication. The emails serve as a trojan horse for the attackers to enter our secured network and rob us of our intellectual properties. Some of the attacks are successful as these remain undetected and they traverse our network to collect the required information. While some are caught at an early stage and data theft can be avoided.
Being a Microsoft Solutions Partner, I see how Microsoft invests billions of dollars in the threat identification and protection industry. The application suite they engineer has the capability to detect the threats and vulnerabilities at the ground stage and automatically take remedial measures to reduce or eliminate the potential interruptions. And this is the secret to stopping the hackers from entering your network; that you identify the malicious activities before they affect you.
Microsoft Microsoft Defender for Office 365 (ATP) is one such application that allows you to safeguard your intellectual resources and gain the capability to detect vulnerabilities and be prepared with the actions to neutralise their effect.
How Microsoft Microsoft Defender for Office 365 Adds a Layer of Security for your Emails
ATP follows a systematic defense–in-depth approach to detect the threats before they impact your organisation. With this approach, the solution analyses threats from the point an email is received to the point it is delivered in the Microsoft 365 environment. 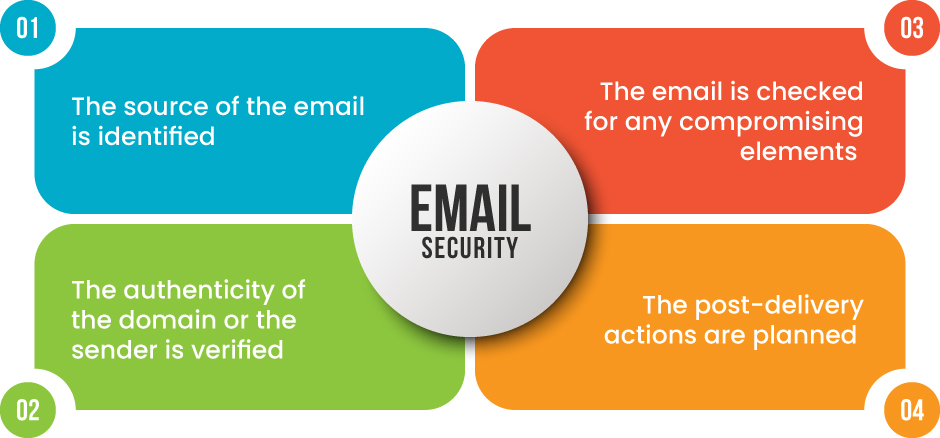
-
Source from which the email originated
ATP checks the reputation of the IP address from which the email was sent. In case anything is found phishy then the email is blocked at the edge only. Microsoft maintains a library of the IP addresses which are often used to send malicious mails. This list is updated on a regular basis so that you can remain ensured that no spam or infected emails enter your ecosystem. The machine learning components are also embedded which keep track of your email traffic and stop emails at the edge if they are originating from any anomalous source.
-
The sender of the email
ATP verifies if the email is spoofed by checking if the email was sent from a forged domain, brand or people. The spoofed emails are those which appear to be coming from an authentic source but are indeed malicious. The anti-phishing policies programmed in Microsoft 365 verifies the authenticity of the domain source. If any email comes from a domain that is owned by your organisation then the application verifies the identity of the sender.
-
The contents of the email
ATP is supplied with safe attachment and safe link capabilities to check the authenticity of the attachments or links sent in the email. These are opened in a sandbox environment and are checked for any malicious activities to ensure that your personal information is secured.
Once the email is delivered
The modern sophistication techniques allow hackers to make the emails bypass the primary checks. They enable them to make the link benign initially and only generate impact once the email message is delivered. With the safe link protection embedded in ATP, the links are checked even if the message is delivered and remedial actions are triggered if need be.
Build a secured infrastructure with Microsoft Defender for Office 365
There are many other areas in which Microsoft ATP enables you to harden the security posture of your organisation. The application is equipped with features and functionalities to shield your collaborative tools such as SharePoint, OneDrive, Teams and more.
Introducing a new application in your business environment can be overwhelming sometimes. We can help you with the deployment of Microsoft Microsoft Defender for Office 365 and offer training to your employees regarding the importance of security and how they should be handling their emails. To initiate a discussion call us at 1300 EXIGOTECH (394 468) or email us at . Let’s join hands to create a secured landscape!
 Australia
Australia Singapore
Singapore Philippines
Philippines India
India Vivek Trivedi | Aug 11, 2020
Vivek Trivedi | Aug 11, 2020




 Exigo Tech - Ask AI
Exigo Tech - Ask AI







