Let’s be honest! Cyber threats are increasing day by day and everyone is aware about it. The question is what steps to take to stay protected from these threats. When cyberattacks take place, the impact isn’t limited to the tech team; it disrupts operations, damages trust and can have a huge impact on an organisation’s reputation.
The Essential Eight, developed by the Australian Cyber Security Centre (ACSC), offers a practical framework that helps businesses prevent breaches before they begin. Designed to block or mitigate the majority of cyberattacks, these Essential Eight controls give organisations a clear path to protecting their systems without the added complexity.
And why I can say this confidently because we at Exigo Tech are fully Essential Eight compliant. Being fully compliant, we know what it takes to implement these controls meaningfully, not just for the sake of it. Our aim isn’t just about helping clients meet a baseline; it’s about empowering them with a cyber strategy that evolves with the threat landscape and supports long-term growth. In this blog, we will discuss the importance and benefits of Essential Eight and how we can help you.
What Is the Essential Eight and Why It Matters to Every Business
The Essential Eight isn’t just a tech checklist, it’s a set of eight practical strategies developed by the Australian Cyber Security Centre (ACSC) to help businesses defend against the most common and damaging types of cyber threats. Each control targets a specific weakness that attackers often exploit. Together, they create a layered defence that makes it significantly harder for a cyberattack to succeed.
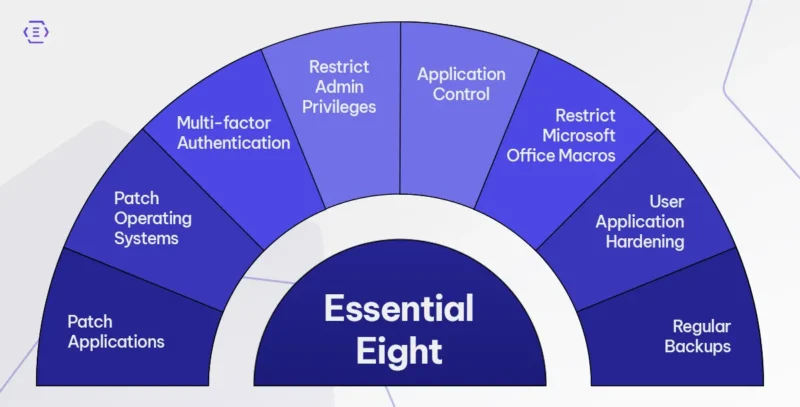
Here’s a quick breakdown of the Essential Eight, and why they matter:
- Patch Applications
Cybercriminals often exploit known vulnerabilities in common software. Regularly patching applications means closing those doors before they are used against you. - Patch Operating Systems
Just like apps, your OS needs to stay updated. Patching ensures you are not leaving your digital doors wide open to known threats. - Multi-factor Authentication (MFA)
Passwords alone aren’t enough. MFA adds a crucial extra layer of identity verification—keeping hackers out, even if they steal credentials. - Restrict Administrative Privileges
Not everyone needs admin access. By limiting privileges, you make it harder for attackers to gain full control, even if they get in. - Application Control
Prevents unauthorised or malicious software from running on your systems. This reduces the risk of ransomware or unapproved apps compromising your environment. - Restrict Microsoft Office Macros
Macros are a favourite tool for attackers to deliver malware. Restricting them helps prevent users from unknowingly triggering harmful code. - User Application Hardening
Disabling unnecessary features in browsers and other applications reduces the attack surface. It’s a simple tweak that adds serious protection. - Regular Backups
If the worst happens, having up-to-date, secure backups means you can recover quickly, without paying ransoms or losing data forever.
What makes the Essential Eight so powerful is its simplicity and real-world effectiveness. It’s not about having the most expensive tools, it’s about using smart, well-proven practices that stop attacks before they become disasters.
At Exigo Tech, we have implemented all Essential Eight internally and we have seen how effective they are.
Benefits of Implementing Essential Eight: How They Translate into Real Business Value
When implemented right, these Essential Eight strategies don’t just prevent threats; they create a more stable, resilient, and trusted business environment. Here’s how:
1. Minimise Disruption, Maximise Continuity
Cyberattacks can bring operations to a halt. With the Essential Eight in place, your risk of ransomware, malware, and other disruptions is dramatically reduced. That means fewer outages, less downtime, and uninterrupted service for your clients.
2. Lower the Cost of Recovery
It’s far cheaper to prevent a breach than to fix the damage afterwards. By patching vulnerabilities, limiting access, and maintaining secure backups, businesses avoid the high costs of data recovery, legal penalties, and reputational damage.
3. Build Customer and Stakeholder Trust
Clients care about security, especially in sectors handling sensitive data. Showing that you are proactively protecting information through a recognised framework like the Essential Eight sends a clear message: trust matters here.
4. Strengthen Compliance Readiness
From privacy regulations to industry-specific standards, compliance is growing more complex. The Essential Eight aligns well with many regulatory expectations, making audits smoother and legal risks smaller.
5. Create a Culture of Security
The framework encourages clear policies, restricted access, regular updates, and accountability. That builds a company-wide security mindset where everyone from leadership to interns understands their role in keeping systems safe.
6. Future-Proof Your Cyber Defence
Threats evolve, and so must your defences. The Essential Eight isn’t a static rulebook, it’s a flexible strategy that adapts as risks change. It gives your business a strong foundation to scale securely, no matter how your tech stack grows.
How Exigo Tech Helps You Implement the Essential Eight
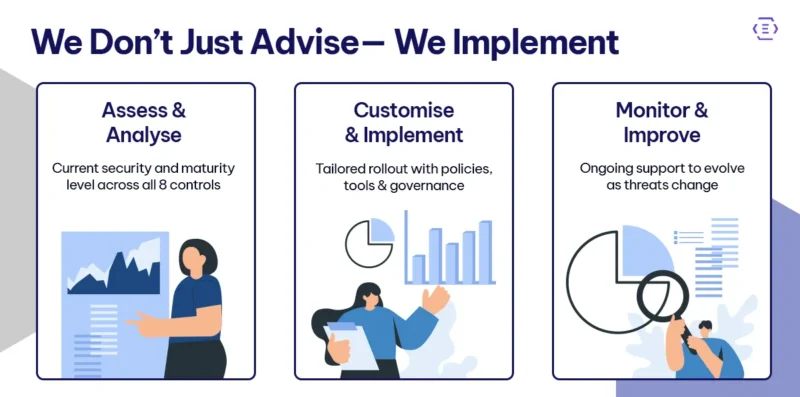
At Exigo Tech, we don’t just talk about the Essential Eight—we live it. As an organisation that is fully Essential Eight compliant, we understand both the technical detail and the business impact behind each control. That gives us a unique advantage when helping our clients adopt the framework in a way that’s relevant, achievable, and sustainable.
We start with a clear assessment of your current maturity level. Whether you have never heard of the Essential Eight or you are already working on it, we help identify where you stand across each of the eight controls. From there, we design a customised implementation plan that fits your systems, business size, compliance needs, and risk profile.
Our support includes:
- Technical implementation of each control, from patching routines to setting up MFA, backups, macro restrictions, and more.
- Policy development and governance to ensure controls are not just in place but are actually being followed.
- Training and awareness programs to build a strong security culture within your team.
- Ongoing monitoring and optimisation, so your protection evolves as threats do.
Since we have implemented the Essential Eight ourselves, we know how to make it achievable even for organisations without large internal IT teams.
If you have any questions or want to clear any doubts, feel free to reach out to us at or call us at 1300 EXIGOTECH (394 468).
 Philippines
Philippines Australia
Australia Singapore
Singapore India
India Brendan Fazel | Jun 16, 2025
Brendan Fazel | Jun 16, 2025





 Exigo Tech - Ask AI
Exigo Tech - Ask AI







